
Security Audit Checklist: Safeguarding Your Digital Ecosystem
.avif)
As organizations navigate the complexities of modern IT environments, they face a myriad of challenges, including sophisticated cyber-attacks that threaten the security and integrity of their digital assets. A cybersecurity audit offers a meticulous examination of an organization's alignment with regulatory standards and the efficacy of its internal security measures. These audits serve a critical function in pinpointing vulnerabilities, safeguarding sensitive data against unauthorized breaches, and upholding a formidable defense mechanism against potential cyber threats.
The Imperative Need for Security Audits
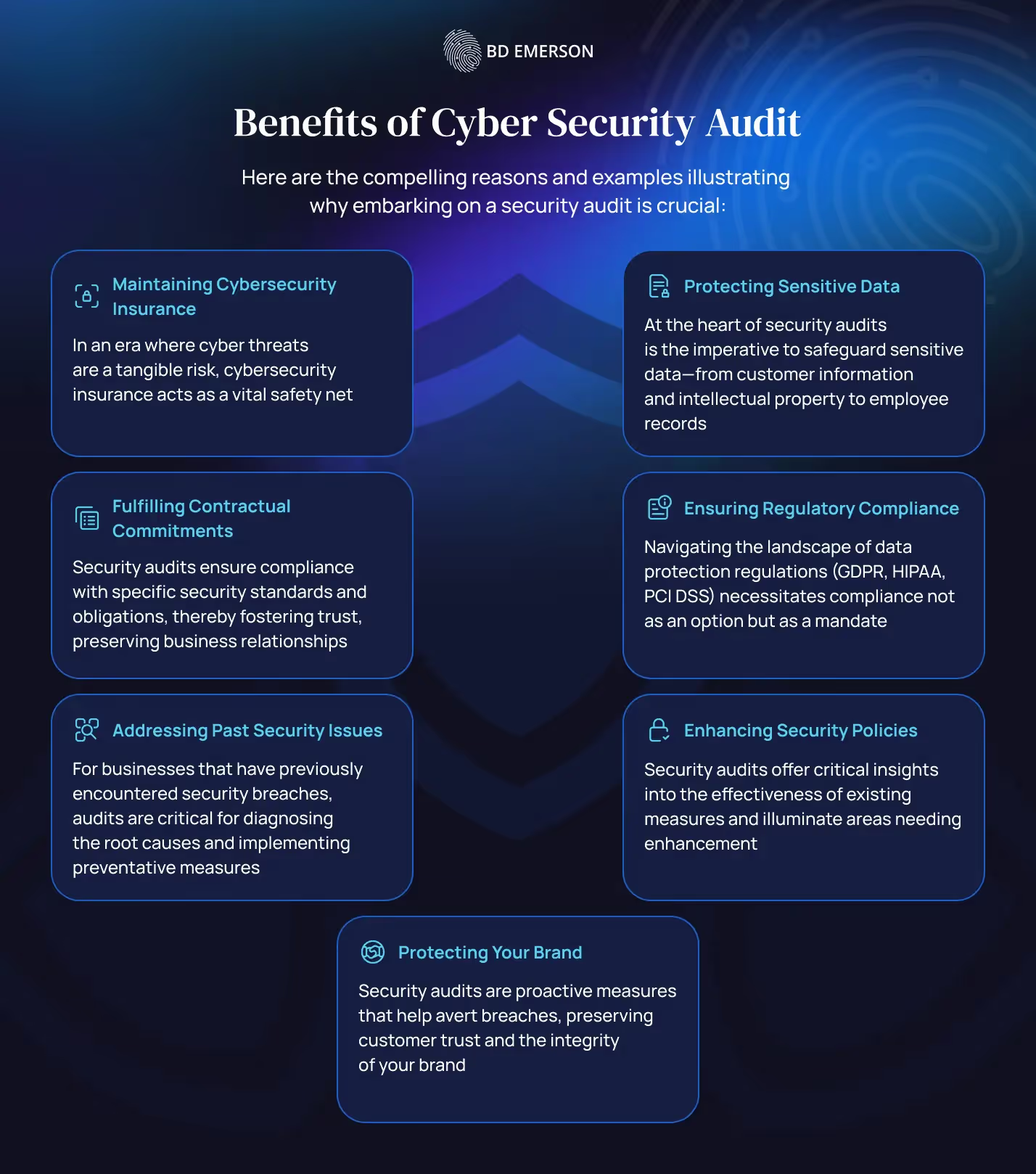
For clients navigating this complex terrain, a security audit emerges not merely as a prudent step but as an indispensable strategy for preserving the integrity and resilience of their operations. Here are the compelling reasons and examples illustrating why embarking on a security audit is crucial:
- Maintaining Cybersecurity Insurance: In an era where cyber threats are a tangible risk, cybersecurity insurance acts as a vital safety net. However, insurers often mandate demonstrable, stringent security practices as a precondition for policy issuance or to maintain reasonable premiums. A thorough security audit showcases to insurers that proactive steps are being taken to minimize risk, potentially leading to more favorable terms or lower premiums.
A retail company, seeking to renew its cybersecurity insurance, undergoes a security audit that identifies and mitigates previously unnoticed vulnerabilities. The audit report facilitates negotiations with the insurer, resulting in lower premiums due to the reduced risk profile.
- Fulfilling Contractual Commitments: Many business engagements, especially those involving sensitive or proprietary data, require adherence to specific security standards as part of contractual agreements. Security audits ensure compliance with these obligations, thereby fostering trust, preserving business relationships, and circumventing contractual disputes.
A software development firm contracts with a government entity requiring ISO 27001 compliance. The firm conducts regular security audits to ensure ongoing compliance, thus upholding the contract and reinforcing the trustworthiness of its services.
- Addressing Past Security Issues: For businesses that have previously encountered security breaches, audits are critical for diagnosing the root causes and implementing preventative measures. These evaluations help to understand how breaches occurred and assess the sufficiency of corrective actions, fortifying defenses against future incidents.
After experiencing a data breach due to compromised email accounts, a financial services provider conducts a security audit that leads to the adoption of multi-factor authentication and advanced monitoring solutions, significantly enhancing its security posture.
- Protecting Sensitive Data: At the heart of security audits is the imperative to safeguard sensitive data—from customer information and intellectual property to employee records. Identifying and remedying vulnerabilities through audits is essential for protecting this data against unauthorized access and mitigating the risks of data breaches.
A healthcare clinic performs a security audit that uncovers inadequate encryption practices for patient records. Remedial measures are swiftly implemented, strengthening data protection and patient confidentiality.
- Ensuring Regulatory Compliance: Navigating the landscape of data protection regulations (GDPR, HIPAA, PCI DSS) necessitates compliance not as an option but as a mandate. Security audits are pivotal in verifying adherence to these regulations, preventing potential fines and legal challenges associated with non-compliance.
An e-commerce platform undergoes a security audit to ensure GDPR compliance, focusing on consent mechanisms and data retention policies. The audit findings lead to enhanced consent protocols, aligning operations with GDPR requirements and avoiding potential penalties.
- Enhancing Security Policies: The dynamic nature of cyber threats demands that security policies evolve in tandem. Security audits offer critical insights into the effectiveness of existing measures and illuminate areas needing enhancement, ensuring that defenses remain robust against emerging threats.
Following a security audit, a manufacturing company revises its security policies to include regular vulnerability and risk assessments and employee training on phishing awareness, significantly reducing its susceptibility to cyber-attacks.
- Protecting Your Brand: Beyond the immediate financial repercussions, the reputational damage from a security breach can have enduring effects. Security audits are proactive measures that help avert breaches, preserving customer trust and the integrity of your brand.
By conducting and publicly reporting on comprehensive security audits, a retail brand demonstrates its commitment to customer data protection, bolstering consumer confidence and loyalty.
Undertaking a security audit is a forward-looking measure that comprehensively assesses and enhances your organization's cybersecurity framework. Whether driven by the need to maintain cybersecurity insurance, fulfill contractual obligations, rectify past vulnerabilities, ensure sensitive data protection, achieve regulatory compliance, update security policies, or safeguard brand reputation, security audits provide the foundation for a secure, resilient, and trusted business operation.
Cyber Security Audit Checklist Tips
.avif)
To navigate the complexities of cybersecurity effectively, organizations are encouraged to adhere to the following cyber security checklist tips:
- Develop a Comprehensive Cybersecurity Policy: The cornerstone of any robust cybersecurity strategy involves the formulation of detailed policies, procedures, and protocols. These documents should encompass all aspects of security, from employee conduct to response protocols for potential incidents.
- Regularly Update Software & Hardware: Keeping software and hardware components up-to-date is essential for closing data security gaps that could be exploited by cybercriminals. Automating the patch management process ensures timely updates and minimizes vulnerabilities.
- Implement Strong Access Controls: Adopting multi-factor authentication and enforcing the principle of least privilege can significantly enhance an organization's security posture by limiting access to sensitive data and systems to only those who require it.
- Encrypt Sensitive Data: Data encryption serves as a critical line of defense, securing information during transmission and storage. By encrypting sensitive data, organizations can prevent unauthorized access and ensure data integrity.
- Conduct Email Awareness Training: Empowering employees with the knowledge to recognize phishing attempts and secure email communications is a vital step in fortifying an organization's security framework.
- Maintain Regular Data Backups: Implementing automated backup solutions provides a safety net in the event of data loss, ensuring the continuity of business operations.
- Monitor Network Traffic: Utilizing advanced monitoring tools to scrutinize network traffic enables organizations to detect and respond to suspicious activities promptly.
- Conduct Regular Vulnerability Assessments: Systematic vulnerability assessments are indispensable for identifying and rectifying security weaknesses before they can be exploited by attackers.
- Review User Access Privileges: Periodically auditing user access rights and making necessary adjustments according to role changes or departures ensures that only authorized individuals have access to critical systems and data.
By integrating these information security audit checklist tips into their security strategies, organizations can not only achieve compliance with regulatory standards but also significantly enhance their overall security posture, safeguarding their digital assets against an ever-changing threat landscape.
How to Perform a Security Audit

Performing a security audit is a structured process that requires meticulous planning and execution to ensure that an organization's information systems are adequately protected against internal and external threats. To achieve this, the audit must be tailored to the specific needs and regulatory obligations of the company. Below is an enhanced outline of how to conduct a security audit, incorporating various methodologies and frameworks.
Define the Audit’s Scope
- Critical Asset Identification: Begin by cataloging all assets within the organization, including hardware, software, data, and network resources. From this list, identify which assets are critical to the organization's operations and contain sensitive information that, if compromised, would pose the greatest risk.
- Audit Boundaries: Establish clear boundaries for the audit, determining whether it will cover the entire IT infrastructure or focus on specific areas, such as network security, application security, or compliance with specific regulations.
- Methodologies and Frameworks: Choose an audit methodology that aligns with the organization's goals and regulatory requirements. Common methodologies include ISO/IEC 27001 for information security management, NIST SP 800-53 for federal information systems, and COBIT for IT governance and management. The chosen framework should guide the audit's scope, objectives, and procedures.
Understand Regulatory Obligations
- Compliance Standards: Different industries are subject to various regulatory standards. For instance, healthcare organizations must comply with HIPAA for patient data, while financial services firms are governed by GLBA and PCI DSS for customer financial information. Identifying these obligations early in the audit process ensures that the audit covers all necessary regulatory compliance aspects.
- Framework Alignment: Align the audit with the relevant compliance frameworks to ensure a comprehensive assessment. For example, GDPR compliance might leverage ISO/IEC 27001 as a framework for managing and protecting personal data.
Identify Risks and Vulnerabilities
- Automated Tools and Assessments: Utilize automated tools and software to scan the organization's information systems for vulnerabilities. These tools can range from network scanners, vulnerability and risk assessment tools, to more specialized software designed to detect specific types of threats.
- Security Posture Assessment: Conduct a thorough assessment of the organization's current security posture, identifying any weaknesses in policies, procedures, and technologies. This assessment should consider both technical vulnerabilities and organizational or process-related weaknesses.
Prioritize Security Concerns
- Risk Analysis: Analyze the identified risks based on the likelihood of occurrence and potential impact on the organization. This analysis will help in prioritizing which vulnerabilities require immediate attention and which can be addressed over time.
- Resource Allocation: Based on the risk analysis, allocate resources effectively to address high-priority concerns first. This may involve patching known vulnerabilities, implementing additional appropriate security controls, or updating security policies and procedures.
- Framework-Specific Prioritization: Some frameworks provide specific guidance on prioritizing security concerns. For example, the NIST Cybersecurity Framework offers categories and subcategories that can help organizations focus on areas that are most critical to their cybersecurity posture.
By meticulously defining the audit's scope, understanding regulatory obligations, identifying risks and vulnerabilities, and prioritizing security concerns, organizations can conduct cybersecurity audits that are congruent with their specific secuirty requirements. This comprehensive approach not only ensures compliance with relevant laws and standards but also strengthens the organization's overall security posture, protecting it from the myriad of cyber threats in today's digital landscape.
Conclusion
A well-conducted security audit is a cornerstone of an effective cybersecurity strategy. By systematically addressing each item on the checklist, organizations can significantly enhance their security posture, protect against cyber threats, and maintain compliance with critical regulatory standards.
Choose BD Emerson
Ready to enhance your organization's cybersecurity posture? BD Emerson offers professional cybersecurity audit consulting services tailored to your unique needs. With our expertise in navigating complex security landscapes, we'll help you conduct thorough audits, identify vulnerabilities, and bolster your defenses. Contact us at info@bdemerson.com to start fortifying your digital ecosystem today.











