
What is Vendor Risk Management (VRM)?

Vendor Risk Management Explained
Vendor risk management is the process of identifying, monitoring and addressing the risks associated with the third-party service providers and vendors that work with your organization. As outsourcing becomes more common, it is more critical than ever to vet the contractors and vendors that your organization does business with in order to protect your organization and its customers’ sensitive information.
Third-party vendors can be attorneys, accountants, product suppliers, marketing teams, and other consultants who store your organization’s sensitive information, including financial details and employee information. Third party vendors without robust information security guardrails can expose your organization to devastating data breaches. A notable data breach occurred in 2021, when one of Facebook’s third party vendors misconfigured its cloud storage and exposed the personal information of over 533 million Facebook users.
VRM is an ever-evolving discipline as regulations change and more companies are collaborating with remote and/or international employees and vendors. Effective VRM will ensure that your organization’s sensitive data is protected, your operations align with compliance requirements, and that your organization will be able to operate continuously, without interruption from cyber attacks and data breaches that could damage your reputation and financial stability.
Your organization should incorporate VRM as a key part of its larger risk management strategy to ensure that information security threats are minimized as much as possible. Read on for insights on how to approach your VRM strategy and boost your organization’s reputation as a security-minded enterprise.
Why is Vendor Risk Management Important?

If you are still on the fence about why a vendor risk management process is essential in today’s business landscape, here are a few more reasons why you should consider implementing VRM.
- Protection of Sensitive Data: By making sure your third-party vendors are properly implementing and securing information security frameworks, you can rest assured that you are doing everything possible to protect the data that your organization shares with them.
- Regulatory Compliance: Several certifications and industry standards require an effective, documented vendor risk management program including SOC 2, ISO/IEC 27001, NIST SP 800-53, GDPR, and HIPAA.
- Operational Continuity: Data breaches can cause lengthy interruptions to an organization’s operations. If you’re effectively managing risks, you’ll prevent disruptions to the critical functions of your organization.
- Reputational Protection: Ensuring that your vendors maintain the highest level of data security standards will demonstrate your commitment to protecting your clients’ sensitive information.
- Financial Stability: Vendor-related incidents can result in huge financial losses due to the cost of remediation, legal fees, and lost revenue.
- Risk Mitigation: A proactive VRM process will ensure that your organization can identify, assess, and mitigate risks associated with vendors, reducing incident likelihood and severity.
- Improved Vendor Performance: An effective VRM program will foster communication and transparency between your organization and its vendors, allowing for a more collaborative relationship.
- Strategic Decision-Making: When you build out your vendor risk management process, you will learn what to look for in vendors and make more informed decisions about contract terms and engagement strategies.
- Visibility and Control: VRM will provide your organization with more insight into how your vendors manage data and the security controls they have in place.
- Incident Response and Recovery: Included in VRM is a robust incident response plan for vendor-related incidents. This will assist with recovering information quickly and effectively.
.avif)
What are the Benefits of Vendor Risk Management?

An example of VRM success can be seen in the aftermath of a cybersecurity attack on JP Morgan Chase & Co. in 2014. The financial institution experienced an attack that resulted in the exposure of personal information from 76 million households and 7 million small businesses. In response, JPMC overhauled its vendor risk management framework in an effort to mitigate future risks and improve the institution’s overall cybersecurity infrastructure.
Since implementing a robust vendor risk management program, JPMC has reported a significant reduction in vendor-related security incidents. This outcome is the result of strict due diligence and constant monitoring, which have ensured the protection of sensitive customer data and promoted customer trust.
Vendor risk management benefits far outweigh the cost of implementing a robust VRM program. Here are several key benefits that your organization should keep in mind:
Enhanced Security
- Improved Data Protection: This one may be a no-brainer, but effective VRM will ensure that your organization’s vendors adhere to strict security practices and keep your sensitive organizational and customer information secured from breaches and unauthorized access. VRM security measures include continuous assessments and monitoring of your vendors’ security operations.
- Early Threat Detection: A proactive VRM program will enable your organization to detect potential security threats early through continuous monitoring of your vendors’ activities. Early detection is essential for preventing incidents altogether or stopping them before they can escalate and cause serious damage.
Achieving Regulatory Compliance
- Compliance Assurance: Many industries have strict rules about how they handle and protect data. Effective vendor risk management makes sure that vendors follow these important regulations, like GDPR, HIPAA, and PCI DSS. Employing an effective VRM process will reduce the chances of facing hefty fines and keeps your organization safe from potential lawsuits.
- Legal Safeguards: By establishing clear contractual terms and service level agreements (SLAs) with security and compliance requirements, your organization can legally protect itself against vendor-related breaches. This clarifies vendor responsibilities and liabilities, ensuring compliance with high standards.
Operational Resilience
- Business Continuity: If third-party vendors are essential for the necessary functions of your organization, vendor risk management can ensure that you maintain operational continuity by minimizing potentially disastrous disruptions from vendor-related incidents.
- Quality Assurance: With a VRM program, your organization will perform regular assessments and audits of its vendors, confirming that the vendors are operating in alignment with your organization's high security standards.
Controlling Costs
- True Cost Efficiency: Many businesses use third party vendors to save on costs associated with hiring specialists in house, but effective VRM has to accompany the hiring of vendors. The costs of recovery and remediation following a data breach could easily outweigh any savings a company makes by outsourcing work to vendors.
- Effective Risk Mitigation: When your organization has a clear understanding of the risks associated with different vendors and requires its vendors to address and minimize these risks, your organization will be able to invest more effectively in secure vendors and avoid getting hit with the legal fees and penalties of vendor incidents.
Strategic Advantage
- Informed Decision-Making: The best vendor risk management programs ensure that the leadership at your organization has all of the necessary information about its vendors so that it can make well-informed decisions with the safety of your organization in mind.
- Competitive Edge: If your organization implements an effective vendor risk management program, it will be able to form more innovative and successful relationships with vendors, which will in turn improve the quality of your services and products.
Improved Reputation
- Customer Trust: Stringent VRM policies will give your customers peace of mind because they will know that they can trust you and the third-party vendors you work with to keep their sensitive information safe.
- Brand Safety: Staying ahead of vendor risks will prevent the negative publicity that follows cyber attacks and data breaches. If you demonstrate that your organization takes vendor risk management seriously, your organization will appeal to security-minded clients and lead to more business in the long run.
What are Third-Party Vendors?
Third-party vendors are businesses that have a relationship with your organization and provide products or services directly to you or your customers. Third-party vendors vary depending on industry. Examples of IT security third-party vendors would be cloud services providers or managed service providers. In human resources, third-party vendors could be companies that offer payroll services or recruitment and staffing agencies. In financial services, a vendor could be a payment processor or credit reporting agency. Third-party vendors don’t necessarily need to provide a product, they could be companies that support your organization’s operations in other ways. It’s more and more common for companies to have a long list of vendors in the post-pandemic world, which makes a well-organized vendor inventory and a robust vendor risk management strategy essential. Though working with third-party vendors can reduce costs associated with hiring specialists in house, they do increase the risk of your organization’s sensitive data being exposed since they will store pertinent information regarding your company on their systems.
Vendor Risk Management Solutions
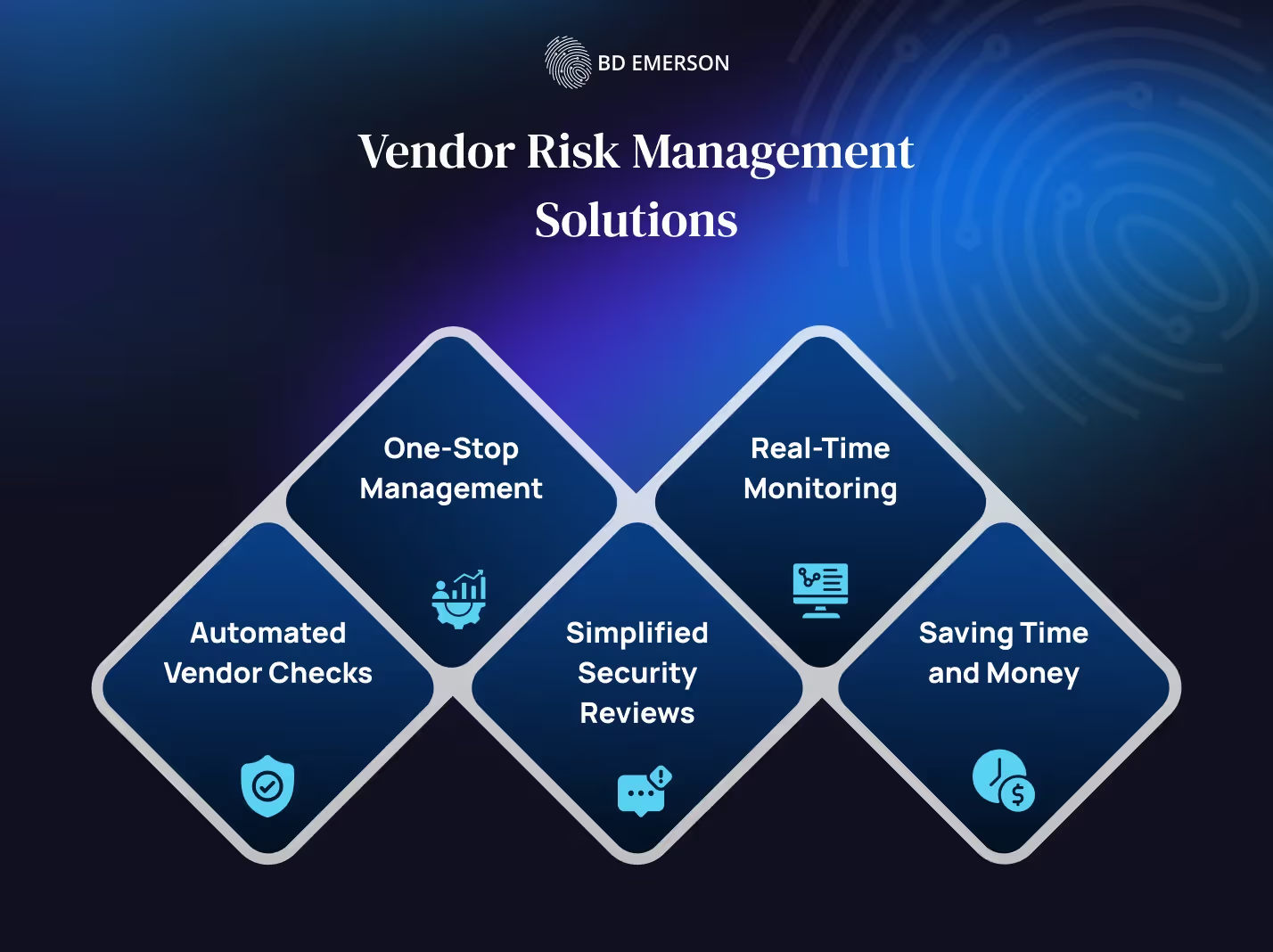
There are plenty of reliable VRM tools on the market that are designed to help companies manage exposure to third-party vendor risks. Before you shop around, it’s important to understand the VRM solutions that these tools will propose as part of their Vendor Risk Management Services and learn why they are important.
Automated Vendor Checks: Imagine not having to manually track down all the vendors your organization uses. This tool automatically finds them and evaluates the risk they pose, using a customizable system that fits your organization’s needs. This saves a ton of time and ensures you’re not missing any critical details while also providing useful vendor risk management metrics.
One-Stop Management: Instead of juggling spreadsheets and multiple systems, you get a single platform where all vendor information is stored and managed. It’s like having a central dashboard that shows you everything you need to know about your vendors, making it easy to keep track and stay on top of things.
Simplified Security Reviews: The tool automates the process of collecting and reviewing security documents from your vendors. It guides you through each step with built-in workflows, ensuring that every review is thorough and consistent, without the repetitive grunt work.
Real-Time Monitoring: It continuously monitors your vendors and sends real-time alerts if something goes off track. This way, you can quickly address any issues as they come up, rather than scrambling after a problem has escalated.
Saving Time and Money: By automating up to 90% of the tasks involved in managing vendor risks, this tool not only saves a lot of time but also cuts down on costs related to manual processes. This efficiency lets your security team focus on more strategic and impactful tasks.
In short, a VRM tool helps keep your vendor management process smooth, efficient, and secure, allowing your team to focus on what really matters.
BD Emerson’s partner Vanta proposes an efficient Vendor Risk Management Tool, designed to streamline and enhance the process of managing third-party vendors. This tool integrates seamlessly with Vanta’s Trust Management Platform, and in combination these tools provide comprehensive capabilities for monitoring and managing security and compliance risks associated with vendors.
.avif)
Next Steps
Compile a VRM Due Diligence Checklist

While many vendor risk management automation tools take care of this for you, it’s important to make a due diligence checklist that outlines important steps your organization must take before contracting with a third-party vendor.
Here are some items that you should consider incorporating into your vendor due diligence checklist:
1. Collect Vendor Information
- Compile basic information about each vendor including contact details
- Assess the financial health of the vendor by reviewing credit ratings or and any finance-related news
- Research if there has been any negative media coverage about the company regarding data breaches or legal issues
2. Check for Compliance and Regulatory Certifications
- If you are planning on working with a vendor in a highly regulated industry, make sure they have the appropriate compliance certifications like HIPAA, GDPR and ISO/IEC 27001
- Verify these credentials and request recent audit reports
3. Assess Security and Data Protection Practices
- Review the vendor’s data security policies and procedures
- Assess how the vendor protects sensitive data, including encryption data handling procedures, and access controls
- Evaluate the vendor’s incident response plan and how they handle security breaches
4. Evaluate Operational Controls
- Ensure the vendor has comprehensive business continuity and disaster recovery strategies in place
- Review performance metrics and Service Level Agreements (SLAs) to confirm that they meet your organization’s standards
5. Analyze Risk Management Practices
- Perform a risk assessment to determine how the vendor identifies, assesses, and mitigates risks
- Assess how the vendor performs its own vendor risk management with its third-party vendors
6. Review Legal and Contractual Terms
- Review the terms of the vendor’s contract and zero in on data protection clauses, termination conditions, and liability limitations
- Ensure the vendor is capable of meeting contractual obligations, especially those related to data security and compliance
7. Establish Vendor Management and Oversight
- Set up processes for continuous monitoring of the vendor’s performance and compliance
- Schedule regular reviews and audits of the vendor’s practices and performance
8. Ensure Secure Access and Connectivity
- Make sure that access to your organization’s data is tightly controlled and monitored
- Evaluate the security of any integrations or connections between your organization’s systems and the vendor’s systems
9. Does the Vendor Provide Employee Training?
- Confirm that the vendor provides regular training on security and compliance to their employees
Start Building Your VRM Program
The type of VRM program your organization chooses to implement will vary widely depending on your organization’s size and the number of vendors it works with. Despite this variation, most vendor management programs follow similar guidelines.
First, you’ll select the type of vendor management software that works best for your organization. We’ll explain the process using Vanta’s Vendor Risk Management Tool as a guide.
Step 1: Set Up Your Account
- Sign Up: If you haven’t already, sign up for a Vanta account and configure it according to your organization’s needs.
- Onboarding: Go through the onboarding process to familiarize yourself with the Vanta platform and its features.
Step 2: Add Vendors
- Automated Discovery: Vanta’s tool can automatically discover vendors used by your employees, which helps identify all third-party services and associated risks
- Manual Addition: You can manually add vendors and provide basic information about each vendor, including their name, category, and contact details.
Step 3: Conduct Initial Risk Assessment
- Risk Rubric: Use Vanta’s risk rubric to evaluate each vendor. This rubric helps prioritize vendors based on their risk levels.
- Initial Questionnaire: Send out initial questionnaires to vendors to gather information about their security practices and compliance status.
Step 4: Perform Security Reviews
- Request Documents: Use the tool to request security documents from your vendors. Vanta’s integration with procurement systems streamlines this process.
- Automated Analysis: Vanta uses AI to analyze the security documents provided by vendors, extracting key findings and identifying potential risks.
Step 5: Continuous Monitoring
- Real-Time Alerts: Enable continuous monitoring to receive real-time alerts about any changes or incidents related to your vendors. This helps in early detection of potential threats.
- Dashboard: Use the centralized dashboard to keep track of all vendor-related activities, assessments, and ongoing risk levels.
Step 6: Risk Mitigation and Remediation
- Action Plans: Based on the findings from the security reviews, create and implement action plans to address identified risks.
- Regular Updates: Ensure that vendors comply with the action plans by requesting regular updates and conducting periodic reassessments.
Step 7: Maintain Documentation and Compliance
- Audit Trails: Keep detailed records of all interactions, assessments, and remediation steps taken with each vendor. This documentation is crucial for compliance audits and regulatory requirements.
- Compliance Assurance: Vanta’s platform helps ensure that your vendors comply with relevant regulations such as GDPR, HIPAA, and PCI DSS.
Step 8: Ongoing Vendor Management
- Regular Reviews: Schedule regular reviews of each vendor’s performance and risk status to ensure they continue to meet your security and compliance standards.
- Training and Awareness: Use Vanta’s resources to provide training and promote security awareness among your team and your vendors.
What are Vendor Risk Management Best Practices?
Regular Assessments: Keep a constant eye on your organization’s vendor risks. This means regularly reviewing and monitoring your vendors to spot any new risks or changes. Staying vigilant and addressing risks early can prevent large breaches down the line.
Strong Contracts: Make sure your contracts with vendors are rock solid, with clear security and compliance requirements. This includes specifying how they should protect data, respond to incidents, and comply with regulations like GDPR and HIPAA. These details ensure that vendors are committed to maintaining high security standards.
Collaboration: Build a good working relationship with your organization’s vendors to tackle any risks together. Open communication helps in sharing information about potential threats and vulnerabilities quickly. This can include joint security exercises and regular meetings to ensure both parties are on the same page.
Training: Both your organization’s internal team and your vendors should be well-versed in security and compliance standards. Regular training sessions help keep everyone updated on the latest threats, best practices, and regulations. This ensures everyone knows what’s expected and how to handle security issues.
Documentation: Keep detailed records of all your vendor interactions, assessments, and any actions taken to address risks. This not only helps in staying compliant but also provides a clear trail of your risk management activities. It’s like keeping receipts for everything, which can be essential during audits.
By following these best practices, you can create a strong vendor risk management program that protects your organization and ensures compliance with all necessary regulations.
Conclusion
Vendor risk management (VRM) is essential for protecting your organization’s sensitive information and ensuring smooth operations. By keeping an eye on and managing risks related to third-party vendors, you can avoid data breaches, meet regulatory requirements, and maintain your organization’s reputation.
Effective VRM helps safeguard your financial stability and strengthens relationships with vendors, making your business more resilient and trustworthy. As companies increasingly depend on external partners, having a solid VRM strategy is crucial. It not only minimizes potential threats but also positions your organization as a reliable and secure business partner. In today's interconnected world, a comprehensive VRM program is a strategic necessity for long-term success.
How Can You Get Started?
BD Emerson offers Third Party Risk Management (TPRM) consulting services, which are expertly designed to empower your organization with the knowledge and tools needed to manage and mitigate these risks effectively. Contact us to learn about BD Emerson’s tailored Vendor Risk Management solutions and how your organization can rapidly implement your own VRM.











